Phishing and File Sharing
Internet thieves have long used file sharing sites and services to host their malicious files. When they do this, they typically use the underlying service to generate download links that anyone can click without logging in to the hosting service.
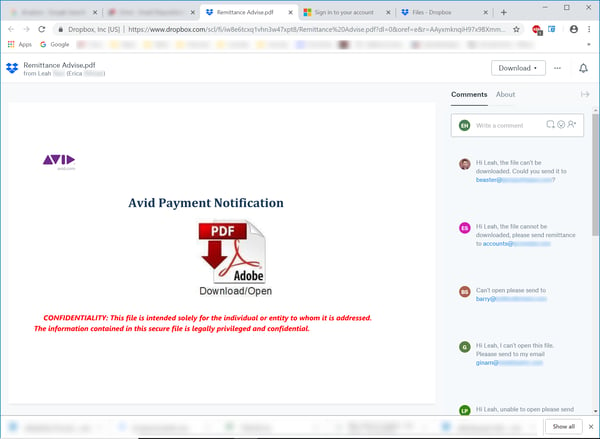
Over the past month we started noticing apparently legitimate Dropbox emails pushing links to files with names suspiciously similar to those routinely used by the bad guys. When we clicked the links to check, however, we were greeted with a demand to log in to the service. That’s typically been a sign that the files involved were legit.
Still, something wasn’t right here. Given the file names presented, we reckoned there was little chance those files were innocuous. So, we decided to log in to Dropbox and check if our hunch was correct. It was.
We spotted a seven Dropbox emails all pushing the same file.
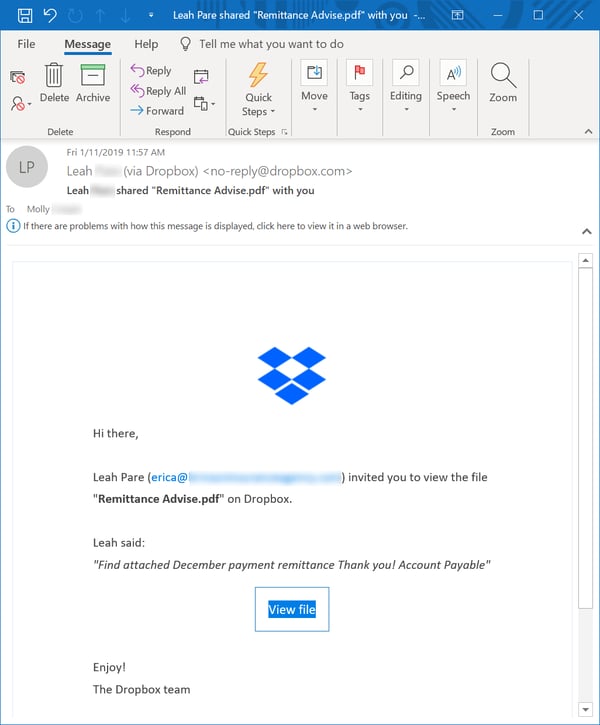
The Wall of Shame
We were also interested to learn that we were not the first to visit to that malicious PDF on Dropbox. Look at the Comments section on the right of that PDF download page.
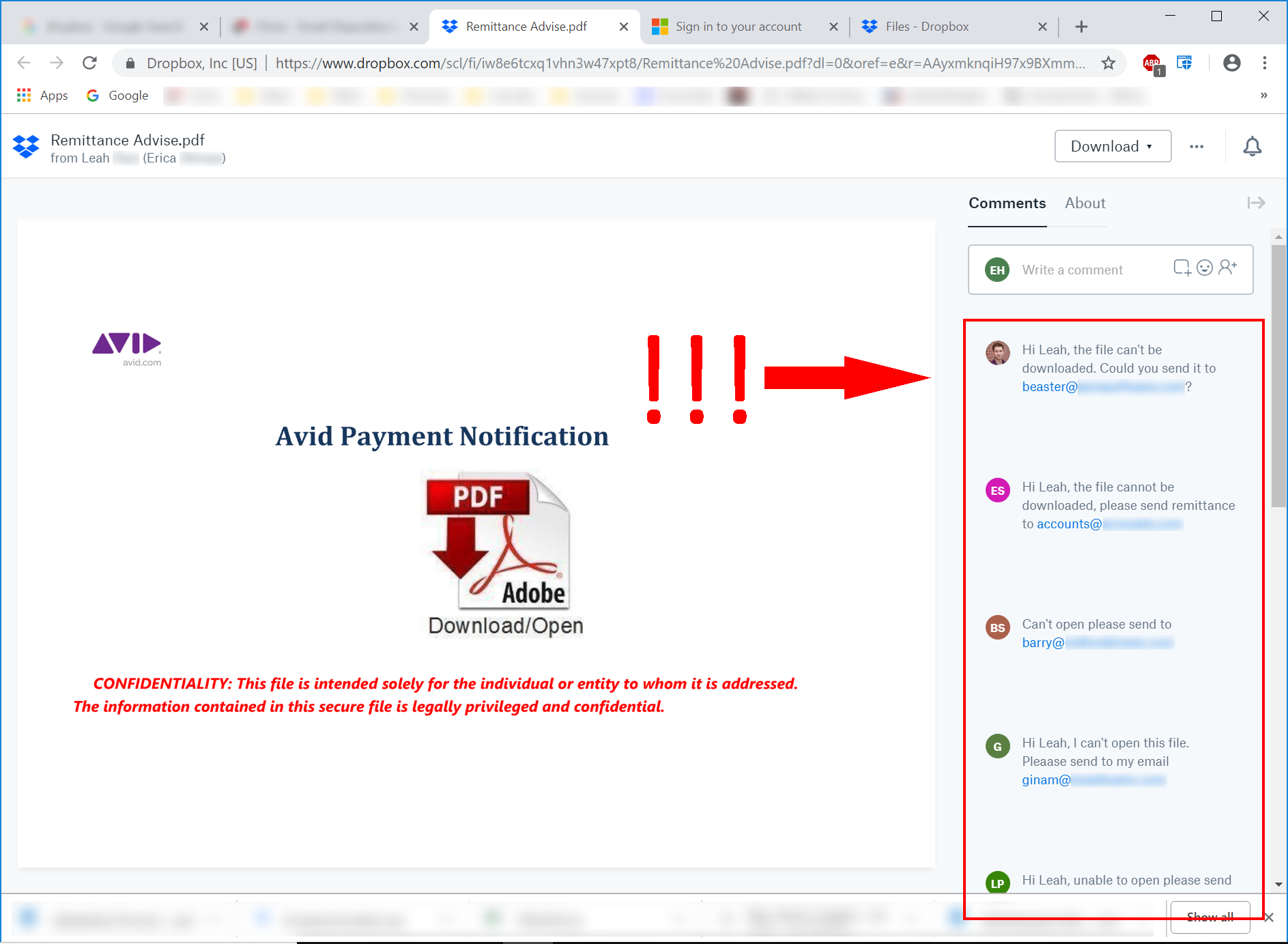
A Calculated Decision
So, the Internet thieves made a calculated decision here: abandon the publicly accessible download links; use Dropbox itself to deliver the links via official Dropbox email notices; then require users to log in to Dropbox. And do it all from a Dropbox account that is undoubtedly compromised.
In doing so, the bad guys undoubtedly narrowed the potential audience for their malicious files (not everyone will have a Dropbox account). But they gained the advantage of camouflaging their malicious links behind Dropbox itself. They got phishing emails that look credible to users (they’re from Dropbox itself), and they reduced the chances that link checkers (now widely used in hosted services like Office 365 and Proofpoint, to mention but two) will be able to follow and identify the malicious links.
And, of course, they also get to enjoy good belly laugh from the spectacle of all those gullible marks outing themselves on Dropbox.
Find Out First
You shouldn’t have to rely on Internet thieves to bait your users into outing themselves. A free Phishing Security Test will quickly tell you who in your organization needs help dealing with cleverly crafted phishing. It will also give you a broader picture of your organization’s vulnerability to phishing attacks, allowing you to roll out New-school Security Awareness Training that gets your users up to speed on how to handle the malicious emails landing in their inboxes every day.
And once your users are “woke” to the threat of phishing, you can provide the Phish Alert Button so they can alert YOU when phishing emails hit their inboxes instead of advertising to the bad guys (and the rest of the world) that they are all-too-vulnerable to phishing campaigns driven by increasingly sophisticated social engineering schemes.”
I suggest you send this reminder to your users. Feel free to edit, copy/paste:
“Internet thieves have come up with another way to trick you! Now they are using sites like Dropbox, Google Drive and other file hosting sites for their evil attacks. They put a malicious file on these sites, and they use that site to send you an invite to log in and open/click on that infected file. The invites look legit because they are. They really came from that site and are identical to the normal invites. So what to look out for?
- Email invites to open a shared file somewhere in the cloud that you did not ask for.
- Emails that require you to log into a site to see something important. Don’t enter anything.
Remember to never click on links in emails that you did not expect or did not ask for. If you decide to log into a file sharing site like Dropbox, enter the address in your browser or use a bookmark you set yourself earlier. Think Before You Click!
Let’s stay safe out there.
—
Cyber Safety Net is a KnowBe4 partner. Reposted with permission from https://blog.knowbe4.com/when-users-add-their-names-to-a-wall-of-shame. Cyber Safety Net – Keeping you safe online. See https://cybersafetynet.net/cyber-security-awareness-training/ to train and strengthen your human firewall. See https://youtu.be/UFpFesrcnvY and https://www.knowbe4.com/security-awareness-training-features/ to learn more.


